Grav <= 1.7.44 - Stored XSS (Authenticated) (CVE-2023-31506)
Introduction
- CVE-ID: CVE-2023-31506
- Vulnerability Type: Stored Cross-Site Scripting (Authenticated)
- Affected Product Code Base: Grav 1.7.44 (or before)
- Affected Component: Affects the CMS text editor (e.g. articles on the main page).
- Attack Type: Remote
- Impact: A remote and authenticated attacker (editor role or permissions to publish), would manage to inject malicious JavaScript code in the form fields to be executed on the users or administrators of the application when accessing the article or another area of the application.
- Attack Vectors: To exploit the vulnerability, you need to be authenticated with a user with editor or publisher access.
Description
A remote and authenticated attacker (editor role or permissions to publish), would manage to inject malicious JavaScript code in the form fields to be executed on the users or administrators of the application when accessing the article or another area of the application.
Disclaimer
The information contained in this disclosure is for educational and research purposes only. I am not responsible for any improper or illegal use of the details provided. It is intended to help improve the security of affected systems. System administrators and software owners are advised to take the necessary steps to mitigate the risks associated with this vulnerability. Unauthorized use of the information to exploit systems without permission is illegal and may have criminal consequences.
Exploitation
In the following evidence, the payload used:
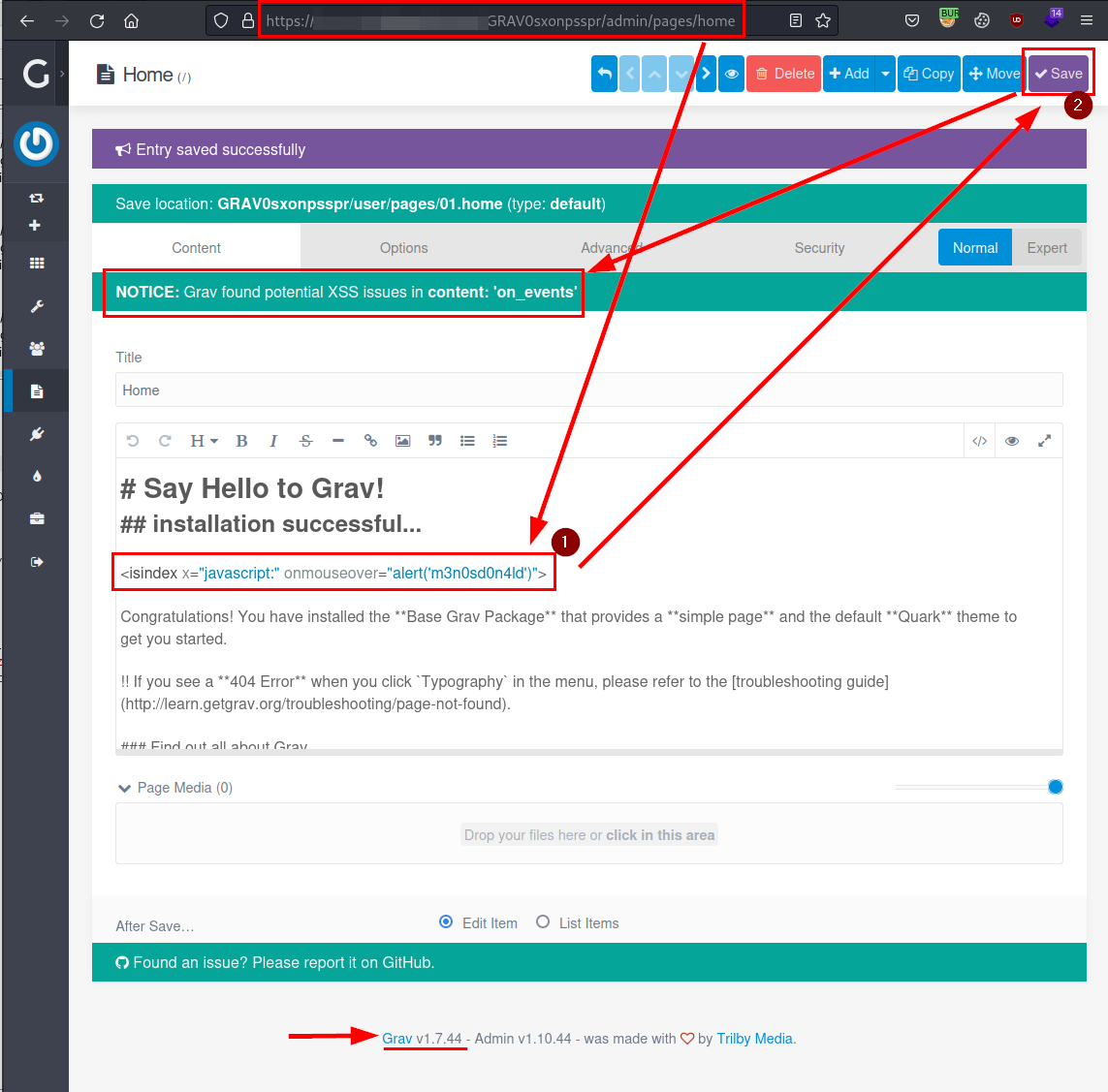
<isindex x="javascript:" onmouseover="alert('m3n0sd0n4ld')">
When saving, the application shows that there is a potential XSS, but has allowed the saving of the file:.
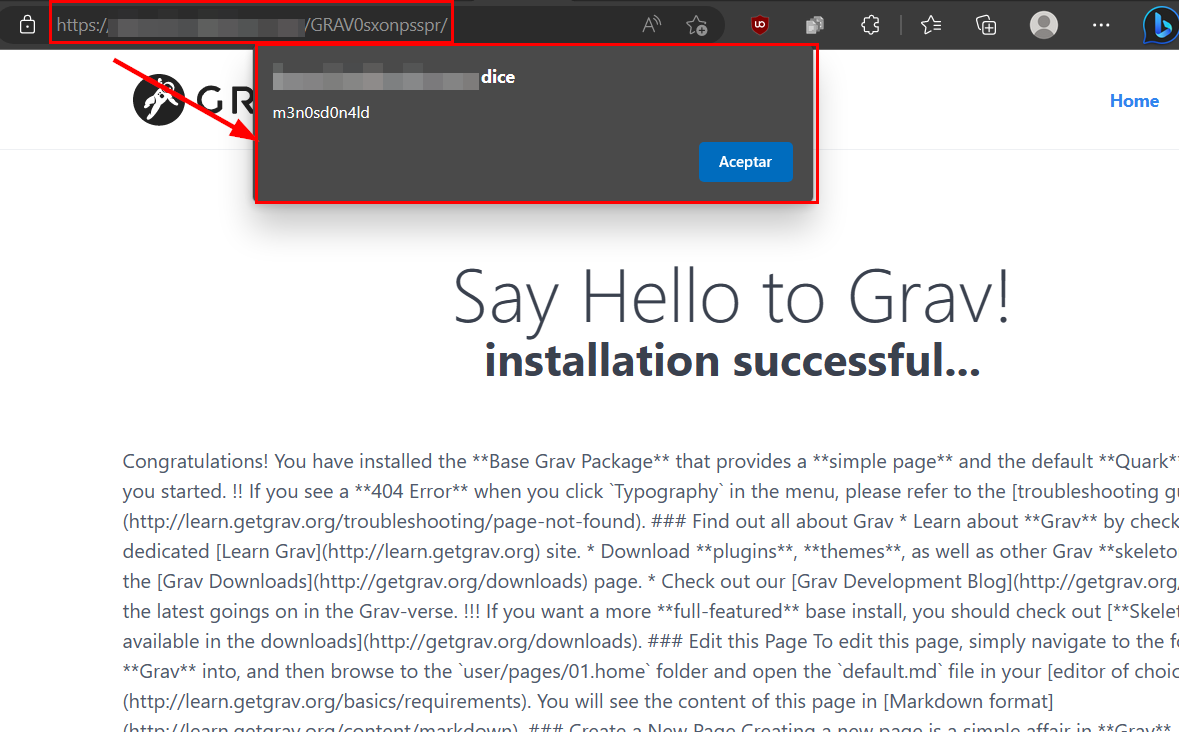
The following illustration, the victim’s browser is shown, in which the reload or access to the section is performed and the javascript code is executed.
Mitigation
- Perform strict server-side validation for all data entered by the user.
- Correctly escape or filter special characters, preventing them from being printable or executed.
- Filter or restrict entries with certain types of characters used in HTML/JavaScript in the different user input fields.
Timeline
- 17/04/2023 - The vendor is notified without response.
- 11/05/2023 - MITRE is notified and the CVE identifier is assigned.
- 07/02/2024 - MITRE is notified of the status, fulldisclosure is authorized.
- 09/02/2024 - NVD published the first details for CVE-2023-31506
Acknowledgments
We would like to thank MITRE CVE for their attention and speed in the procedures with the CVE identifier.