StreamIO HackTheBox Writeup
Scanning
We run nmap on ports with scripts and software versions and enumerate subdomains streamIO.htb and watch.streamIO.htb:
Enumeration
We access to port 80 and found an Microsoft IIS server.
We access to streamio.htb:
We enumerate an corporative email:
Also, we enumerate others users:
We testing with Oliver user and working!
We run dirsearch tool at watch.streamio.htb, we found PHP common files:
We access to “search.php” file:
We can see an hidden button for login, but not working…
We return to streamio.htb, we execute dirsearch tool at streamio.htb with only PHP files and common directories:
We testing with guessing for the users enumerated, but not working.
We register an account, but doesn’t work either.
Exploitation
We testing with SQL Injection in the authentication form… Yeah! It’s website is vulnerable to SQL Injection Stacked queries.
We use SQLMap tool, Great, It’s working!
Found databases:
Found relevant tables:
Extract credentials:
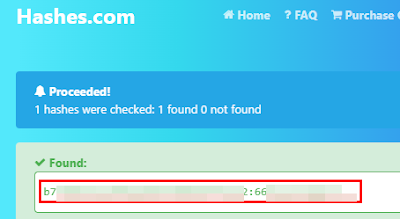
We cracking credentials of the all databases and we test the credentials in the login form of streamio.htb:
We try to access in the “admin” directory and we have access as administrator user:
We identified that the sections go by the variable, we tried to load some system file (LFI) in the “movie” parameter but without success.
We tried fuzzing with wfuzz, to see if we can enumerate any other parameter that we can exploit some deficiency in the site.
We enumerate the “debug” parameter:
We tried to access, but it indicates that it is only available for developers.
We go back to SQL Injection, check our permissions to see if we can read or write any files. We see that we are in luck, we are a DBA user:
Try os-shell and enable xp_cmdshell, but it is very slow, so first try to mount a fake SMB resource to try to sniff the traffic and hijack NetNTLMv2 hashes.
NetNTLMv2 hash hijack of “DC$” account:
We tried to crack the hash, but without success.
We go back to the url and the “debug” file, we try to execute LFI and we see that it accepts the wrappers, managing to enumerate the database credentials.
But we have no visibility to MSSQL, so we will have to look for another alternative.
We go back to fuzzing with wfuzz in the admin directory, we find a file called “master.php”:
So we extract the code and we see that it has a functionality over include that would allow to load content of a file.
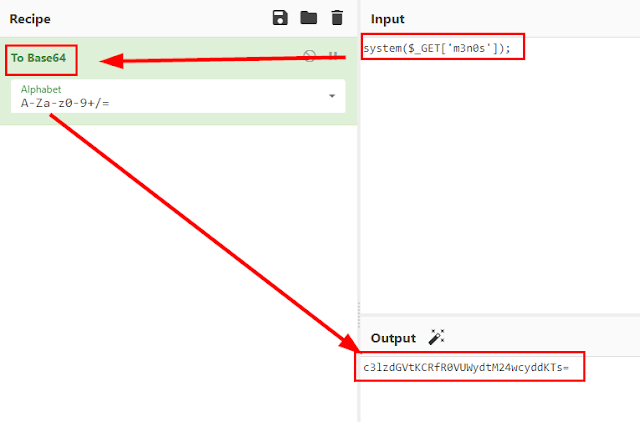
So we try to take advantage of the wrappers to create a base64 include and this code to execute the following code
Code:
curl -s -k -X 'POST' -H 'Content-Type: application/x-www-form-urlencoded' -b 'PHPSESSID=uacidljb5r1uos72ui2lflttu9' --data-binary "include=data://text/plain;base64,c3lzdGVtKCRfR0VUWydtM24wcyddKTs=" 'https://streamio.htb/admin/?debug=master.php&m3n0s=whoami'
Proof of Concept:
We use the nishang script, raise a server with python and get a session on the victim machine.
We do not have access to read the flag, but we remember that there was a backup database that we did not reach from outside. So we do port forwarding and connect to it.
We extract the users, we find “nikk37”, this user has an account on the machine.
Cracking password of user “nikk37”:
We connect via winrm and read the user flag:
Privilege Escalation
We checked our permissions:
We see other users:
We launch the winpeas tool to do system recognition, we list the “Firefox” directory displayed in our user, sometimes it is possible to obtain credentials.
Use Firefox Decrypt tool: https://github.com/unode/firefox_decrypt
We use the tool, it asks for a password but we leave it blank and get credentials for 4 users:
We visited the site “slack.streamio.htb”, but there seems to be nothing.
Nothing, we install bloodhound and extract the information from the Active Directory to see if we find anything interesting to escalate privileges.
We see that with the user “jdgood” we would be able to get into the group “core Staff” and read the laps password:
We read the explanation provided by bloodhound, install the PowerView.ps1 script and execute the following commands:
$SecPassword = ConvertTo-SecureString 'JDg0dd1s@d0p3cr3@t0r' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('streamio\JDgodd',$SecPassword)
Add-DomainObjectAcl -Credential $Cred -TargetIdentity "Core Staff" -principalidentity "streamio\JDgodd"
Add-DomainGroupMember -identity "Core Staff" -members "streamio\JDgodd" -credential $Cred
Now, we run the laps.py script with the “Jdgodd” credentials and we will get the administrator password:
We connect with the credentials of administrator by evil-winrm, we read the root flag but it is not in its directory, we look for the file “root.txt” and we find it hosted on the desktop of the administrator “Martin” and we read the flag.
About
David Utón is Penetration Tester and security auditor for web and mobiles applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks.